Digital Tampering Detection (E.g., Photoshop, AI-generated Digitals)
Prevent fraud by identifying receipt images that have been digitally manipulated. Taggun's Digital Tampering Detection feature helps ensure the integrity of promotions and expense reports by catching attempts to modify receipt images before submission.
Key Capabilities
- Image-Editing Software Detection: Identifies receipts that have been edited with image manipulation software (e.g., Photoshop).
- Metadata Analysis: Detects suspicious changes in image or PDF metadata.
- Copy-Paste Detection: Identifies where parts of the receipt image have been copied and pasted.
- Fake Digital receipt detection: Identifies receipts that are generated by AI tools or templates.
How It Works
When a file is submitted, our Taggun's engine performs the following analyses:
- Error Level Analysis (ELA): Scans for inconsistencies in image compression that may signal tampering.
- Copy-Paste Detection: Flags areas where parts of the image have been duplicated, often used in fraud.
- Metadata Inspection: Reviews the image or PDF metadata for any signs of editing.
- Visual artefact detection: Detects digital markers on the image
Receipts are flagged for potential tampering should be manually reviewed or rejected.
Common Scenarios
Here are some typical scenarios you may encounter when detecting digital tampering. These examples illustrate how Taggun’s tampering detection system flags manipulated receipts—even when sophisticated editing software or techniques are used.
Note that Taggun is equipped to handle many more cases beyond the examples provided here.
1. Receipt with Digital Markers (e.g., WhatsApp/Photoshop Overlays)
In this scenario, the receipt image shows visible digital markers to partially cover certain information on a receipt—such as a WhatsApp editing tool or Photoshop software—that indicate image editing. These markers can be detected through metadata analysis and visual artefact detection

A photo of a receipt with digital markers.

TAGGUN identifies the digital markers as potential fraud.
2. Receipt with White Textbox Overlay
This scenario occurs when a user digitally obscures parts of a receipt by overlaying text on a white background. The white box may be used to hide key details (such as the total amount or merchant information) and is detected via the whiteBoxTampered flag.

A photo of a receipt with white colour textbox overlay.

TAGGUN identifies the white colour textbox overlay as potential fraud.
3. Receipt with Copy-Pasted Digits
In this example, the tampering involves selectively copying and pasting individual digits or parts of numbers (e.g., altering pricing or total amount). The system flags these changes as suspicious based on duplicate detection in specific image regions.

A photo of a receipt with copy-pasted digits ($10.50).

TAGGUN identifies the copy-pasted digits on the image as potential fraud.
4. Error Level Analysis (ELA) Detection
In this example, the system uses Error Level Analysis (ELA) to pinpoint discrepancies in the image’s compression levels. Inconsistent compression artifacts can indicate that parts of the receipt image have been modified. This technique is particularly effective at uncovering subtle tampering that may not be obvious through visual inspection alone.

A photo of a receipt with inconsitent compression artifacts.

TAGGUN identifies the inconsitent compression artifacts on the image as potential fraud.
5. Fake Digital Receipt Detection
This scenario focuses on detecting receipts generated by AI tools or templates closely resembling real receipts, rather than authentic, real-world images. These synthetic images often display repetitive or unnatural textures that set them apart from genuine photographic receipts.
Due to the complexity of this emerging fraud, Taggun currently restricts this feature to low-size PNG files under 800KB to minimize false positives. This limit helps maintain a high level of accuracy when flagging potential AI-generated fakes while reducing the chance of incorrectly classifying legitimate digital receipt screenshots as fraudulent.
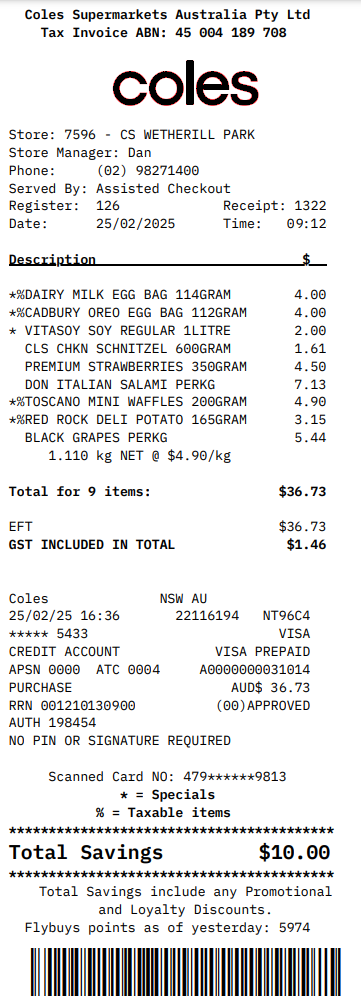
An example of an AI-generated receipt with synthetic text and formatting.
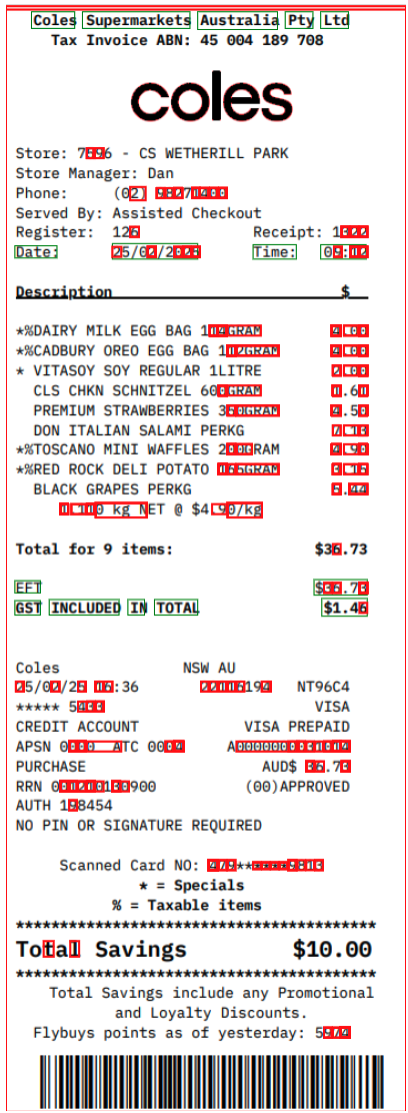
TAGGUN flags repetitive patterns of digitally generated content.
6. AI Generated Receipt Detection
Detects receipts created by AI tools like ChatGPT, DALL-E, or Midjourney. These AI-generated receipts can be extremely difficult for humans to distinguish from authentic photographs, but have distinct characteristics that automated detection system can identify.

An example of an AI-generated receipt using SORA
An example of an AI-generated receipt using Chat GPT
Setup Process
1. Contact Taggun
Reach out to [email protected] to enable this feature for your account.
2. Endpoints
This feature is available in all verbose and validation endpoints. It will be returned automatically once enabled for your account.
Understanding Response Properties
Main Properties
| Field Name | Type | Description |
|---|---|---|
entities.tamperDetection | object | Contains the tampering detection results. |
entities.tamperDetection.data.isTampered | boolean | Indicates whether the receipt has been tampered with. |
entities.tamperDetection.data.tamperedScore | number | The calculated score indicates the likelihood of tampering (0 to 0.99). |
entities.tamperDetection.data.details | object | Additional details regarding the tampering detection analysis. |
Tampering Detection Details Properties
These fields are for informational purposes only and may change. Direct mapping is not recommended.”
| Field Name | Type | Description |
|---|---|---|
elaTampered | boolean | Indicates if Error Level Analysis detected inconsistencies in image compression. |
metadataTampered | boolean | Shows whether suspicious changes were found in the image or PDF metadata. |
copyPasteTampered | boolean | Indicates if areas of the image appear to have been copied and pasted. |
whiteBoxTampered | boolean | Indicates if white box tampering techniques were detected. |
duplicates | array | List of duplicate areas found in the image. Empty if no duplicates are found. |
rectangles | array | List of suspicious rectangular areas in the image. |
percentageBlocksTampered | number | Percentage of image blocks that show signs of tampering. |
normalisedOverallMeanDiff | number | A normalised score representing the overall difference in image characteristics. |
clusterPercentage | number | Percentage of clustered tampered areas. |
blocksTampered | number | Total number of image blocks showing signs of tampering. |
Updated 2 months ago